ob-p-a2a-bulk
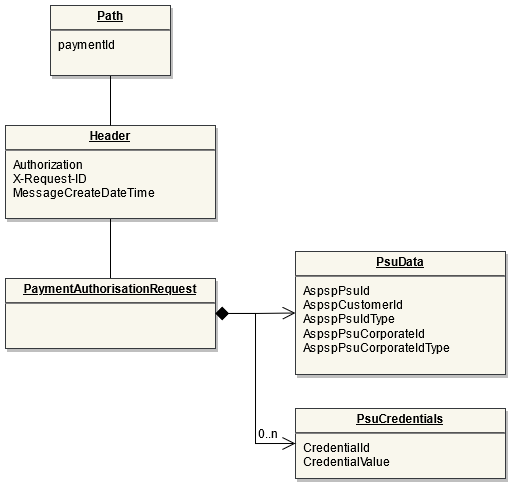
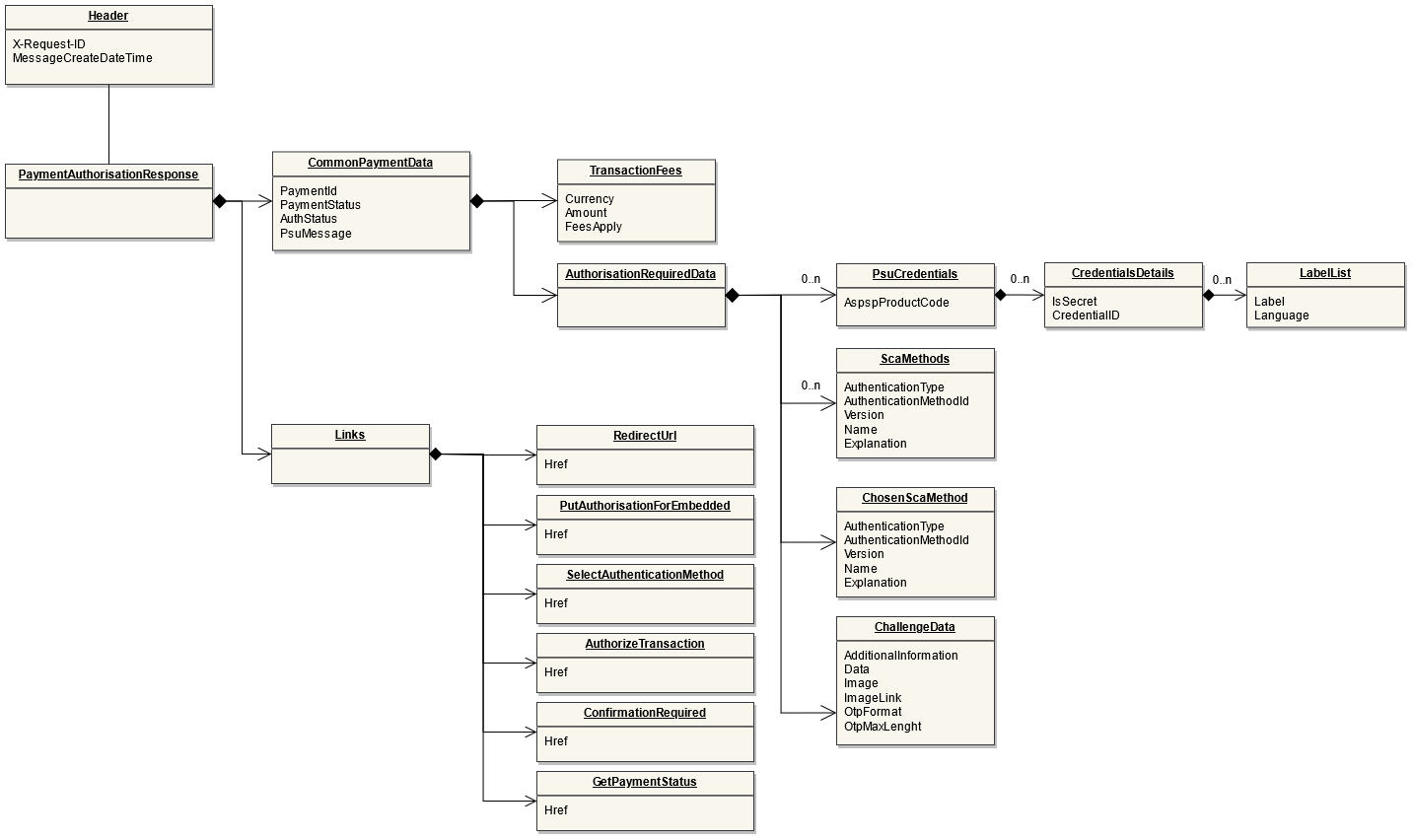
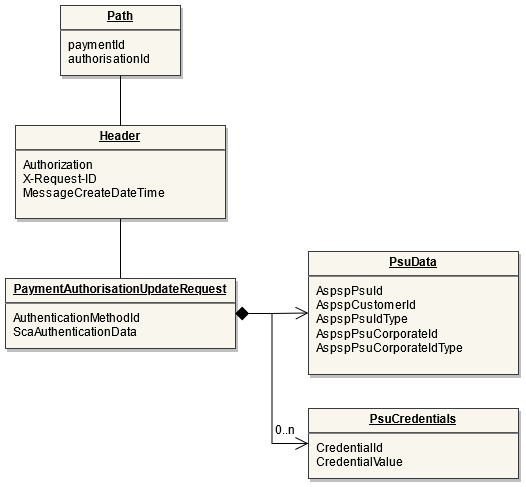
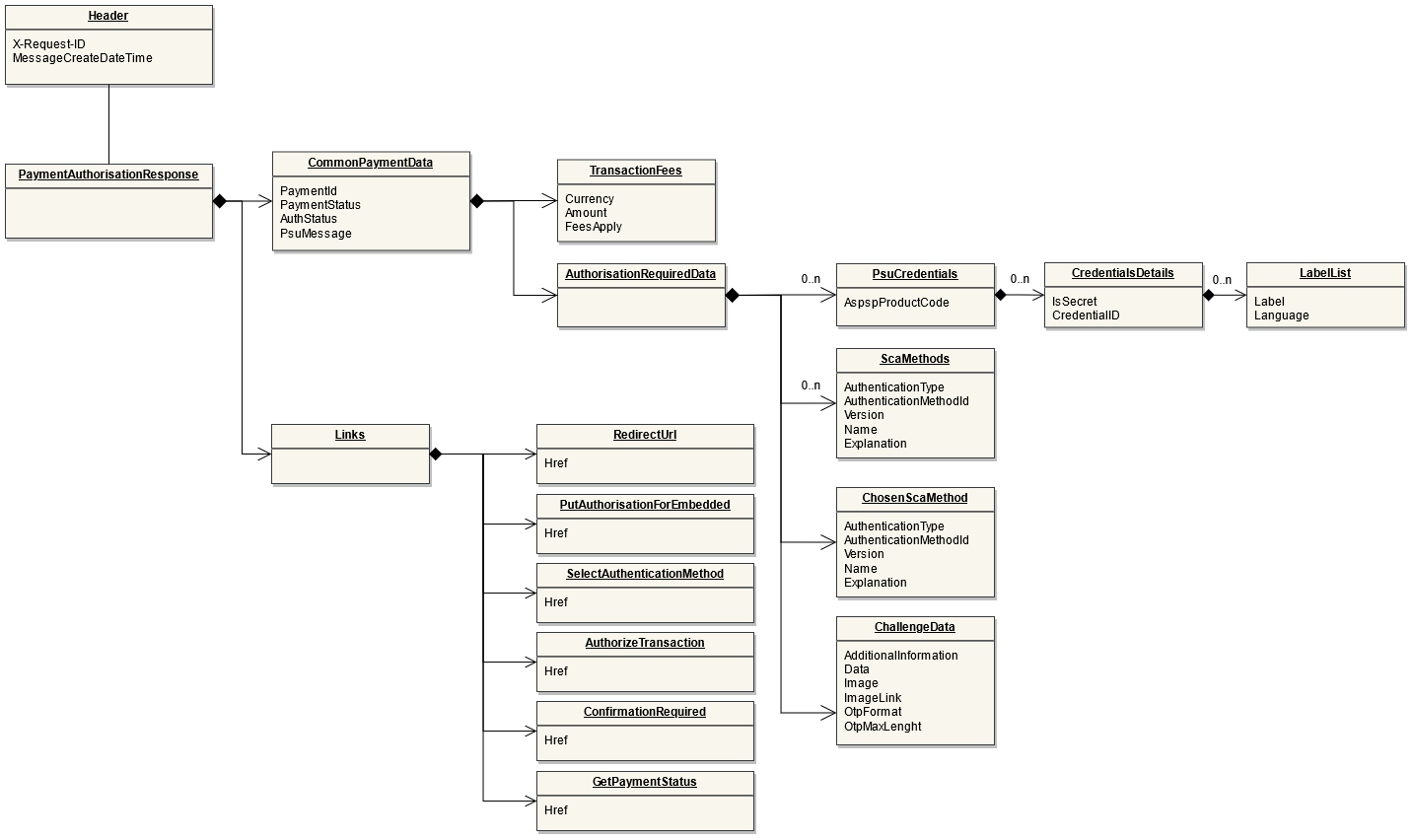
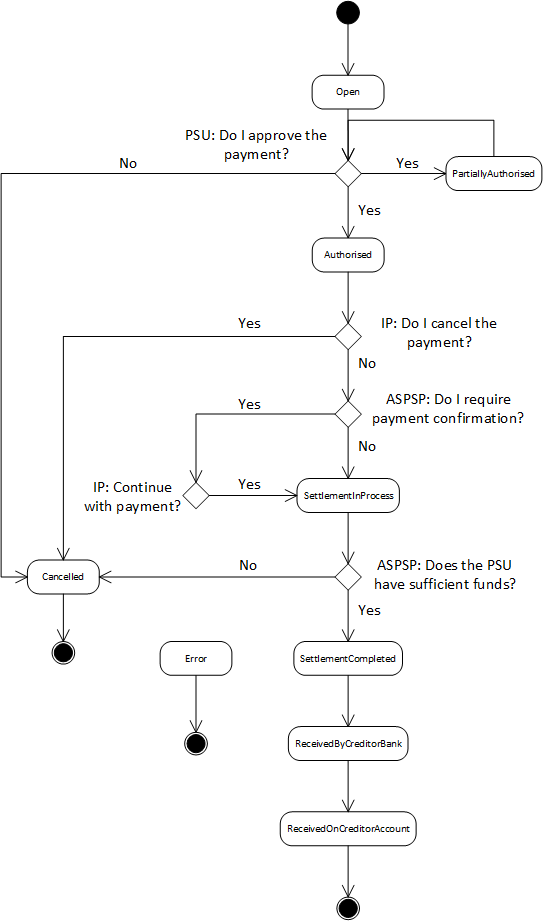
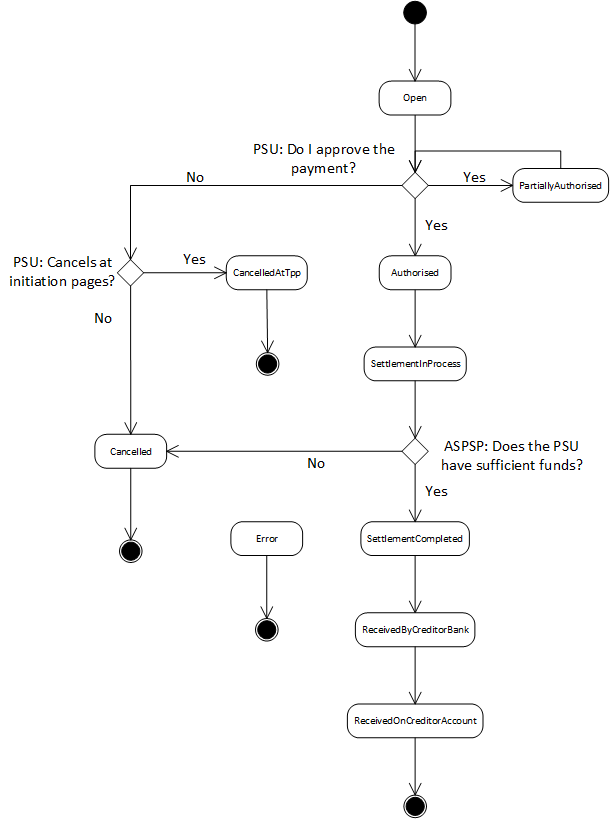
The Payment Process "Bulk payment" allows to send multiple payments at once: individual payments are bundled together into one single transaction. The Bulk Payment is used for processing refunds on PIS payments on the Routingservice. Once the refund is requested by the customer and accepted by the Initiating Party, or initialized by the Initiating Party, the IP can directly use the Refund API for Online Refunds to initiate either a single or up to ten payments on the Routing Service (using the Bulk Payment Interface).
Please also check the Refund Section
The base URL for the Payment Initiation Service API is: /xs2a/routingservice/services/ob/pis/v3
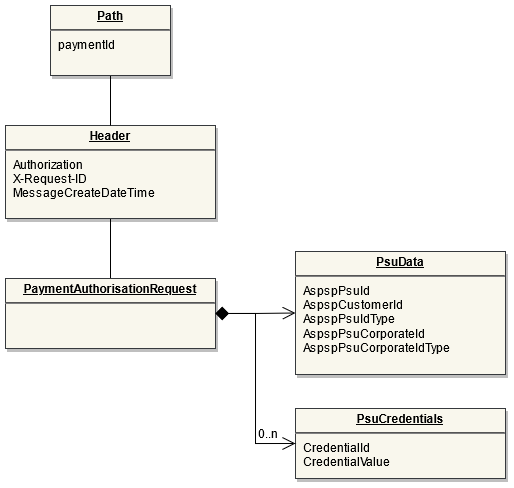
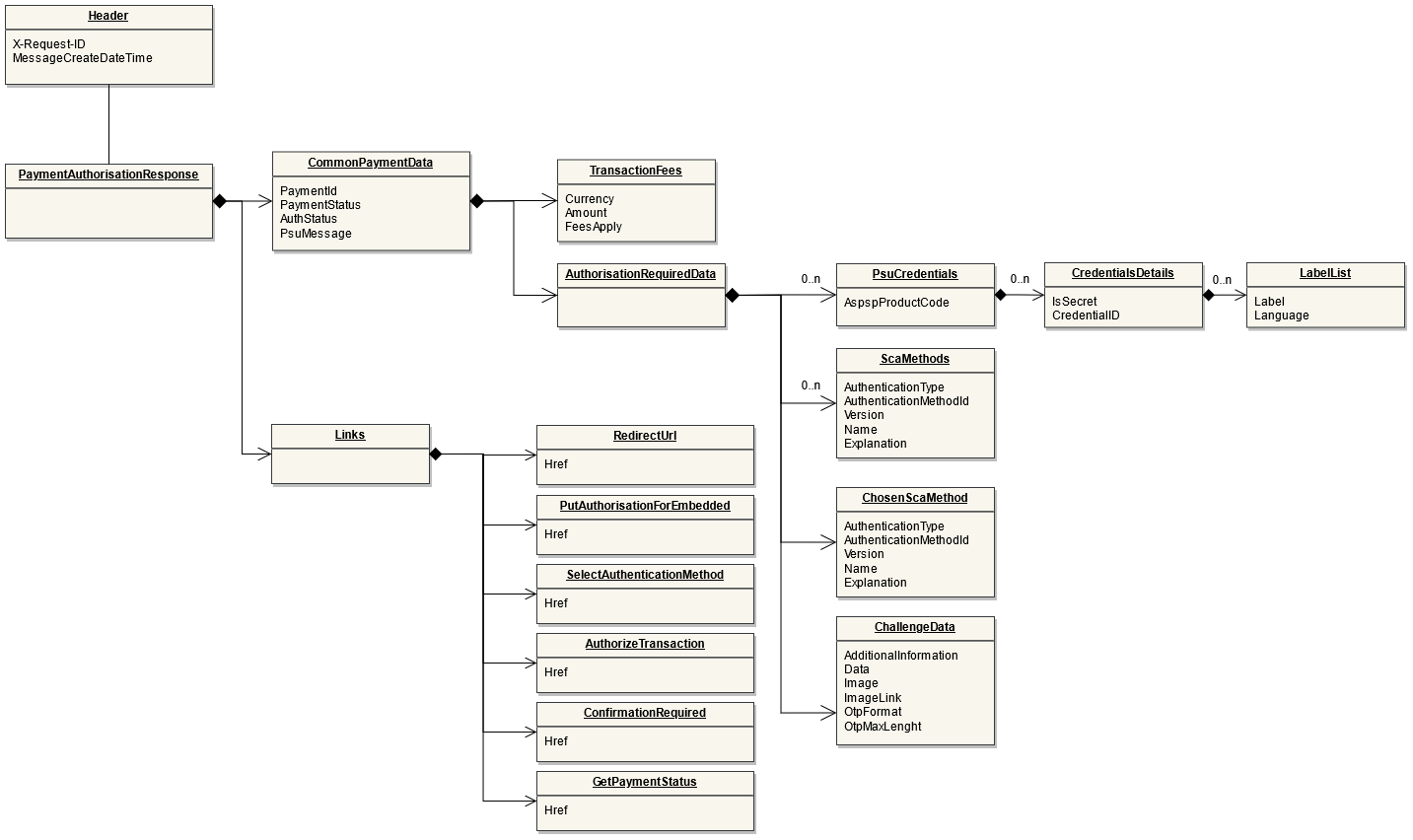
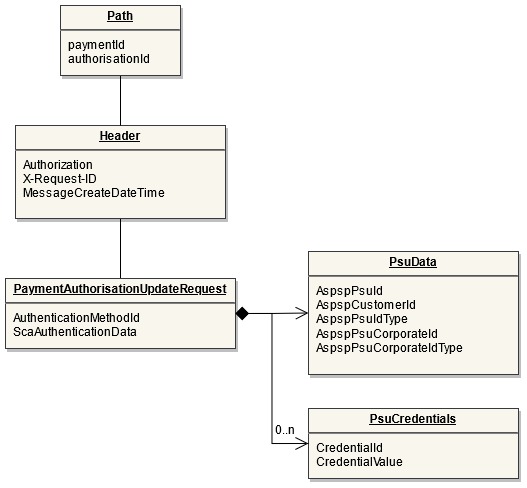
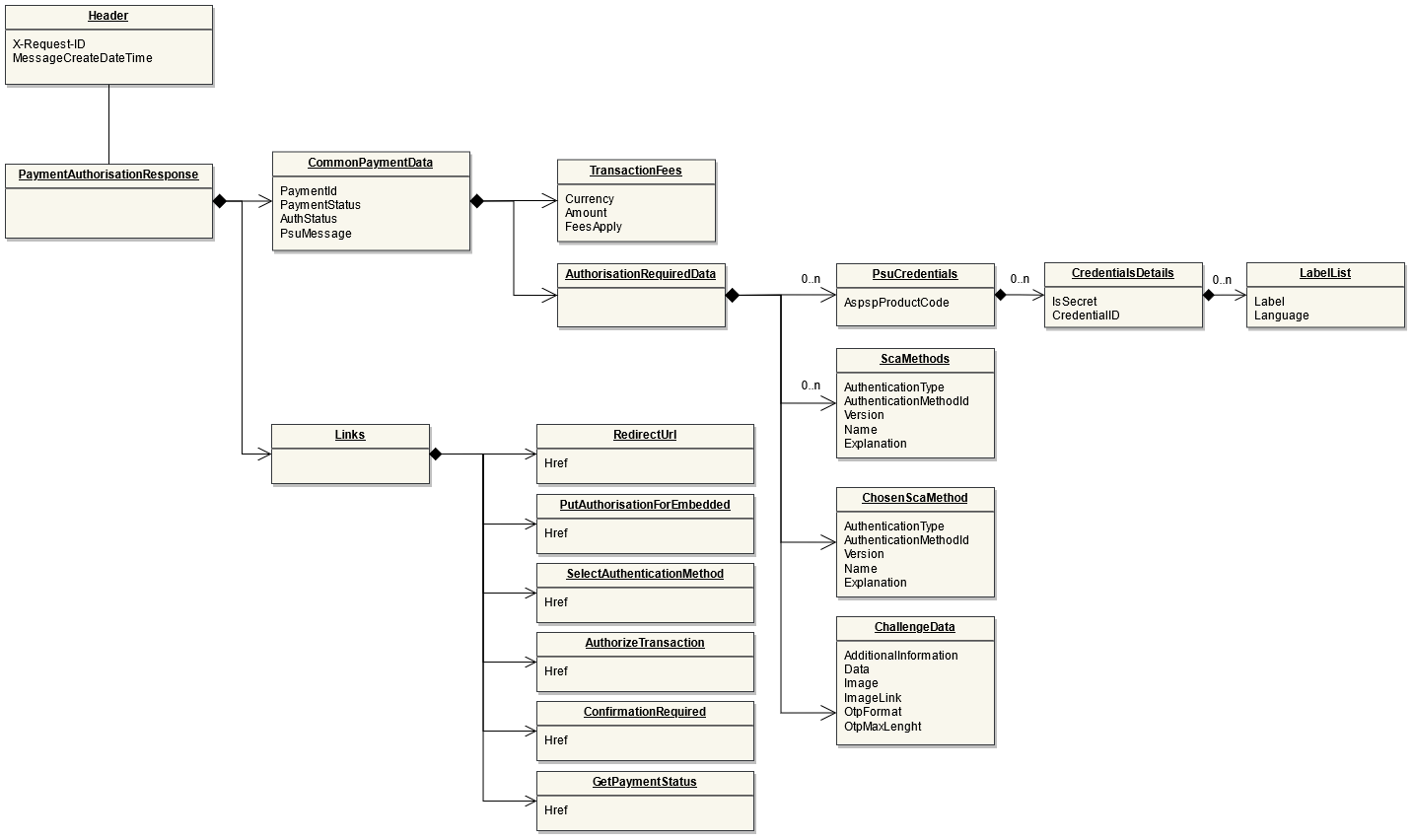
POST Bulk Payments
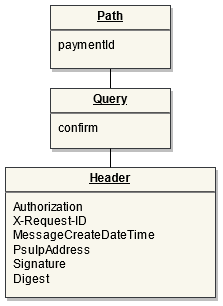
Endpoint: POST /bulk-payments
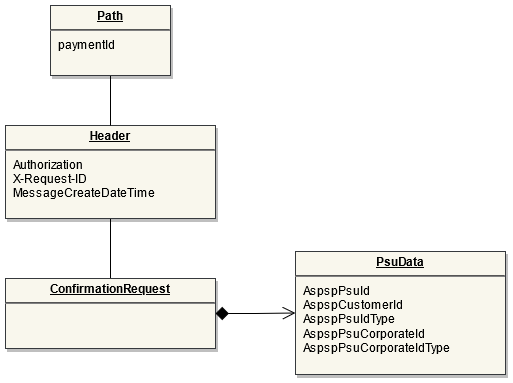
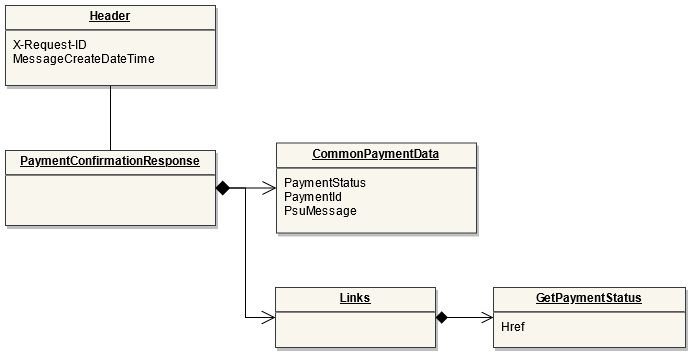
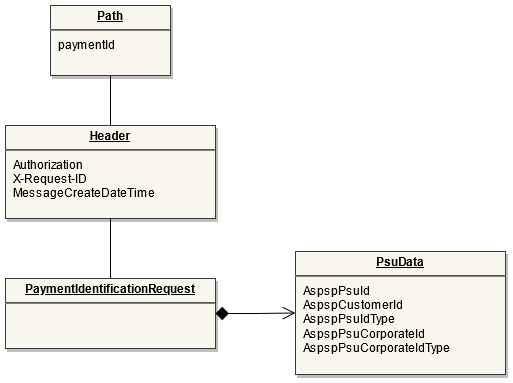
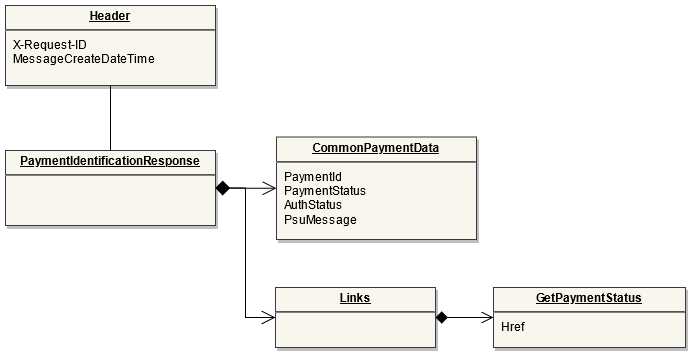
This endpoint is used by the Initiating Party to set up payment initiation for an ASPSP.
Example
Example of a bulk payment request body.
{
"PaymentProduct": [
"PSD2-SCT"
],
"PaymentProductChangeable": false,
"PsuData": {
"AspspId": "20210",
"AspspProductCode": "string",
"Country": "FR"
},
"CommonPaymentData": {
"PreferredScaMethod": [
"Redirect"
],
"DebtorInformation": {
"Name": "Rob Smith",
"Agent": "EG8BCROZMX8",
"Account": {
"SchemeName": "IBAN",
"Identification": "DE89370400440532013000",
"Currency": "EUR"
}
},
"ChargeBearer": "DEBT",
"Payments": [
{
"EndToEndId": "ID-0123456789-A",
"Amount": {
"Amount": "123.45",
"Currency": "EUR"
},
"CreditorInformation": {
"Name": "John Smith",
"Account": {
"SchemeName": "IBAN",
"Identification": "DE89370400440532013012",
"Currency": "EUR"
},
"Agent": "UZWHIKRXVHT",
"UltimateCreditor": "John Media Shop U"
},
"RemittanceInformation": "Remittance Information",
"RemittanceInformationStructured": {
"Reference": "Remit-23-43-42",
"ReferenceType": "structured",
"ReferenceIssuer": "Reference Issuer"
}
},
{
"EndToEndId": "ID-0123456789-B",
"Amount": {
"Amount": "78.56",
"Currency": "EUR"
},
"CreditorInformation": {
"Name": "Simon Walker",
"Account": {
"SchemeName": "IBAN",
"Identification": "NL98INGB6709624056",
"Currency": "EUR"
}
},
"RemittanceInformation": "Remittance Information"
}
]
}
}