API version 2.34.1
REST API V2 - 2.34.1
Version 2.34.0 to 2.34.1
What's New
No API added.
What's Changed
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/account-guarantor
Response:
- Changed property data (object ContractMember)
- Changed property customer (object Customer)
- Added property lastUpdateDate (string)
- Changed property company (object Company)
- Added property lastUpdateDate (string)
- Changed property customer (object Customer)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/account-owner
Response:
- Changed property data (object ContractMember)
- Changed property customer (object Customer)
- Added property lastUpdateDate (string)
- Changed property company (object Company)
- Added property lastUpdateDate (string)
- Changed property customer (object Customer)
GET /issuers/{issuerId}/accounts/{accountReference}/account-guarantor
Response:
- Changed property data (object ContractMember)
- Changed property customer (object Customer)
- Added property lastUpdateDate (string)
- Changed property company (object Company)
- Added property lastUpdateDate (string)
- Changed property customer (object Customer)
GET /issuers/{issuerId}/accounts/{accountReference}/account-owner
Response:
- Changed property data (object ContractMember)
- Changed property customer (object Customer)
- Added property lastUpdateDate (string)
- Changed property company (object Company)
- Added property lastUpdateDate (string)
- Changed property customer (object Customer)
GET /issuers/{issuerId}/companies/{customerReference}
Response:
- Changed property data (object Company)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/companies/external-customers/{issuerCustomerExternalReference}
Response:
- Changed property data (object Company)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/companies/{customerReference}/addresses/{addressReference}
Response:
- Changed property data (object Company)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/companies/{customerReference}/addresses/external-addresses/{issuerAddressExternalReference}
Response:
- Changed property data (object Company)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/companies/external-customers/{issuerCustomerExternalReference}/addresses/{addressReference}
Response:
- Changed property data (object Company)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/companies/external-customers/{issuerCustomerExternalReference}/addresses/external-addresses/{issuerAddressExternalReference}
Response:
- Changed property data (object Company)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/card-contracts/external-card-contracts/{issuerCardContractExternalReference}/cardholder
Response:
- Changed property data (object Customer)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/card-contracts/{cardContractReference}/cardholder
Response:
- Changed property data (object Customer)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/contracts/external-contracts/{issuerContractExternalReference}/contract-owner
Response:
- Changed property data (object Customer)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/contracts/{contractReference}/contract-owner
Response:
- Changed property data (object Customer)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/corporate-contracts/{contractReference}/contract-owner
Response:
- Changed property data (object ContractMember)
- Changed property customer (object Customer)
- Added property lastUpdateDate (string)
- Changed property company (object Company)
- Added property lastUpdateDate (string)
- Changed property customer (object Customer)
GET /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/contract-owner
Response:
- Changed property data (object ContractMember)
- Changed property customer (object Customer)
- Added property lastUpdateDate (string)
- Changed property company (object Company)
- Added property lastUpdateDate (string)
- Changed property customer (object Customer)
GET /issuers/{issuerId}/customers/external-customers/{issuerCustomerExternalReference}
Response:
- Changed property data (object Customer)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/customers/{customerReference}
Response:
- Changed property data (object Customer)
- Added property lastUpdateDate (string)
GET /issuers/{issuerId}/companies
Response:
- Changed property data (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
POST /issuers/{issuerId}/companies
Response:
- Changed property data (object CreateCompanyResponse)
- Changed property company (object Company)
- Added property lastUpdateDate (string)
- Changed property company (object Company)
GET /issuers/{issuerId}/customers
Response:
- Changed property data (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
POST /issuers/{issuerId}/customers
Response:
- Changed property data (object CreateCustomerResponse)
- Changed property customer (object Customer)
- Added property lastUpdateDate (string)
- Changed property customer (object Customer)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/contract
Response:
- Changed property data (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
GET /issuers/{issuerId}/accounts/{accountReference}/contract
Response:
- Changed property data (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
GET /issuers/{issuerId}/card-contracts/external-card-contracts/{issuerCardContractExternalReference}/contract
Response:
- Changed property data (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
GET /issuers/{issuerId}/card-contracts/{cardContractReference}/contract
Response:
- Changed property data (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
GET /issuers/{issuerId}/corporate-contracts/{contractReference}/corporate-employee-accounts/{accountReference}
Response:
- Changed property data (object CorporateEmployeeAccount)
- Changed property customers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property customers (array)
GET /issuers/{issuerId}/corporate-contracts/{contractReference}/corporate-employee-accounts/external-accounts/{issuerAccountExternalReference}
Response:
- Changed property data (object CorporateEmployeeAccount)
- Changed property customers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property customers (array)
GET /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/corporate-employee-accounts/external-accounts/{issuerAccountExternalReference}
Response:
- Changed property data (object CorporateEmployeeAccount)
- Changed property customers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property customers (array)
GET /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/corporate-employee-accounts/{accountReference}
Response:
- Changed property data (object CorporateEmployeeAccount)
- Changed property customers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property customers (array)
POST /issuers/{issuerId}/corporate-contracts/{contractReference}/add-corporate-employee-cards-accounts
Request body :
- Changed property addCorporateEmployeeCardsAndAccounts (object CreateCorporateContractRequest.AddCorporateEmployeeCardsAndAccounts)
- Changed property corporateEmployeeCards (array)
- Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
- Changed property cardContract (object CreateCorporateContractRequest.CardContract)
- Added property cardClass (string)
- Changed property cardContract (object CreateCorporateContractRequest.CardContract)
- Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
- Changed property corporateEmployeeCards (array)
POST /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/add-corporate-employee-cards-accounts
Request body :
- Changed property addCorporateEmployeeCardsAndAccounts (object CreateCorporateContractRequest.AddCorporateEmployeeCardsAndAccounts)
- Changed property corporateEmployeeCards (array)
- Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
- Changed property cardContract (object CreateCorporateContractRequest.CardContract)
- Added property cardClass (string)
- Changed property cardContract (object CreateCorporateContractRequest.CardContract)
- Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
- Changed property corporateEmployeeCards (array)
GET /issuers/{issuerId}/contracts/external-contracts/{issuerContractExternalReference}
Response:
- Changed property data (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
GET /issuers/{issuerId}/contracts/{contractReference}
Response:
- Changed property data (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/corporate-contract
Response:
- Changed property data (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
GET /issuers/{issuerId}/accounts/{accountReference}/corporate-contract
Response:
- Changed property data (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
GET /issuers/{issuerId}/card-contracts/external-card-contracts/{issuerCardContractExternalReference}/corporate-contract
Response:
- Changed property data (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
GET /issuers/{issuerId}/card-contracts/{cardContractReference}/corporate-contract
Response:
- Changed property data (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
GET /issuers/{issuerId}/corporate-contracts/{contractReference}
Response:
- Changed property data (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
GET /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}
Response:
- Changed property data (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
POST /issuers/{issuerId}/corporate-contracts/create-corporate-contract
Request body :
- Changed property addCorporateEmployeeCardsAndAccounts (array)
- Changed items (object CreateCorporateContractRequest.AddCorporateEmployeeCardsAndAccounts)
- Changed property corporateEmployeeCards (array)
- Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
- Changed property cardContract (object CreateCorporateContractRequest.CardContract)
- Added property cardClass (string)
- Changed property cardContract (object CreateCorporateContractRequest.CardContract)
- Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
- Changed property corporateEmployeeCards (array)
- Changed items (object CreateCorporateContractRequest.AddCorporateEmployeeCardsAndAccounts)
POST /search-contracts
Response:
- Changed property data (array)
- Changed items (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
- Changed items (object Contract)
POST /issuers/{issuerId}/contracts/search
Response:
- Changed property data (array)
- Changed items (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
- Changed items (object Contract)
GET /issuers/{issuerId}/customers/external-customers/{issuerCustomerExternalReference}/contracts
Response:
- Changed property data (array)
- Changed items (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
- Changed items (object Contract)
GET /issuers/{issuerId}/customers/{customerReference}/contracts
Response:
- Changed property data (array)
- Changed items (object Contract)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCustomers (array)
- Changed items (object Contract)
GET /issuers/{issuerId}/companies/{customerReference}/corporate-contracts
Response:
- Changed property data (array)
- Changed items (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
- Changed items (object CorporateContract)
GET /issuers/{issuerId}/companies/external-customers/{issuerCustomerExternalReference}/corporate-contracts
Response:
- Changed property data (array)
- Changed items (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
- Changed items (object CorporateContract)
POST /search-corporate-contracts
Response:
- Changed property data (array)
- Changed items (object CorporateContract)
- Changed property contractCompanies (array)
- Changed items (object Company)
- Added property lastUpdateDate (string)
- Changed items (object Company)
- Changed property contractCustomers (array)
- Changed items (object Customer)
- Added property lastUpdateDate (string)
- Changed items (object Customer)
- Changed property contractCompanies (array)
- Changed items (object CorporateContract)
What's Deprecated
No API deprecated.
API version 2.34.0
REST API V2 - 2.34.0
Version 2.33.2 to 2.34.0
What's New
No API added.
What's Changed
POST /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/post-payment-operation
Request body :
Added property specificFields (object)
POST /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/post-reimbursement-operation
Request body :
Added property specificFields (object)
POST /issuers/{issuerId}/accounts/{accountReference}/post-payment-operation
Request body :
Added property specificFields (object)
POST /issuers/{issuerId}/accounts/{accountReference}/post-reimbursement-operation
Request body :
Added property specificFields (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/insurance-contracts/{insurancePackageReference}
Response:
Changed property data (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/operations/{operationId}
Response:
Changed property data (object Operation)
Added property specificFields (object)
POST /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/inquire-operation
Response:
Changed property data (object Operation)
Added property specificFields (object)
GET /issuers/{issuerId}/accounts/{accountReference}/insurance-contracts/{insurancePackageReference}
Response:
Changed property data (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/{accountReference}/operations/{operationId}
Response:
Changed property data (object Operation)
Added property specificFields (object)
POST /issuers/{issuerId}/accounts/{accountReference}/inquire-operation
Response:
Changed property data (object Operation)
Added property specificFields (object)
POST /search-transactions
Request body :
Added property relatedTransaction (object)
POST /issuers/{issuerId}/transactions/{transactionId}/dispute
Parameters:
Added: WL-Username in header
PATCH /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}
Request body :
Changed property hierarchyOutgoingCreditTransferFeature (object ModifyHierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object ModifyAccountRequest.AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}
Response:
Changed property data (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/insurance-contracts
Response:
Changed property data (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/operations
Parameters:
Changed: printOnStatement in query
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/statements/last/operations
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/statements/next/operations
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/statements/{cycleClosureDate}/operations
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
PATCH /issuers/{issuerId}/accounts/{accountReference}
Request body :
Changed property hierarchyOutgoingCreditTransferFeature (object ModifyHierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object ModifyAccountRequest.AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
GET /issuers/{issuerId}/accounts/{accountReference}
Response:
Changed property data (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/{accountReference}/insurance-contracts
Response:
Changed property data (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/{accountReference}/operations
Parameters:
Changed: printOnStatement in query
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
GET /issuers/{issuerId}/accounts/{accountReference}/statements/last/operations
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
GET /issuers/{issuerId}/accounts/{accountReference}/statements/next/operations
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
GET /issuers/{issuerId}/accounts/{accountReference}/statements/{cycleClosureDate}/operations
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
POST /search-operations
Response:
Changed property data (array)
Changed items (object Operation)
Added property specificFields (object)
GET /issuers/{issuerId}/customers/{customerReference}
Parameters:
Changed: embed in query
POST /issuers/{issuerId}/contracts/{contractReference}/replace-customer
Response:
Added property data (object)
Deleted property contract (object)
POST /issuers/{issuerId}/contracts/external-contracts/{issuerContractExternalReference}/replace-customer
Response:
Added property data (object)
Deleted property contract (object)
POST /issuers/{issuerId}/cards/external-cards/{issuerCardExternalReference}/block-and-replace
Request body :
Changed property replaceCardRequest (object ReplaceCardRequest)
Changed property cardContract (object ReplaceCardRequest.CardContract)
Changed property card (object ReplaceCardRequest.CardContract.Card)
Added property panSequenceNumber (string)
POST /issuers/{issuerId}/corporate-contracts/{contractReference}/add-corporate-contract-entity
Request body :
Changed property customers (array)
Changed items (object CreateCorporateContractRequest.Customer)
Changed property addresses (array)
Changed items (object CreateCorporateContractRequest.Address)
Changed property addressUsages (array)
Changed items (object CreateCorporateContractRequest.AddressUsage)
Added property entityRequestCorrelationId (string)
Added property entityType (string)
POST /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/add-corporate-contract-entity
Request body :
Changed property customers (array)
Changed items (object CreateCorporateContractRequest.Customer)
Changed property addresses (array)
Changed items (object CreateCorporateContractRequest.Address)
Changed property addressUsages (array)
Changed items (object CreateCorporateContractRequest.AddressUsage)
Added property entityRequestCorrelationId (string)
Added property entityType (string)
POST /issuers/{issuerId}/corporate-contracts/{contractReference}/add-virtual-cards-accounts-service
Request body :
Changed property customers (array)
Changed items (object CreateCorporateContractRequest.Customer)
Changed property addresses (array)
Changed items (object CreateCorporateContractRequest.Address)
Changed property addressUsages (array)
Changed items (object CreateCorporateContractRequest.AddressUsage)
Added property entityRequestCorrelationId (string)
Added property entityType (string)
POST /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/add-virtual-cards-accounts-service
Request body :
Changed property customers (array)
Changed items (object CreateCorporateContractRequest.Customer)
Changed property addresses (array)
Changed items (object CreateCorporateContractRequest.Address)
Changed property addressUsages (array)
Changed items (object CreateCorporateContractRequest.AddressUsage)
Added property entityRequestCorrelationId (string)
Added property entityType (string)
POST /issuers/{issuerId}/cards/external-cards/{issuerCardExternalReference}/replace
Request body :
Changed property cardContract (object ReplaceCardRequest.CardContract)
Changed property card (object ReplaceCardRequest.CardContract.Card)
Added property panSequenceNumber (string)
POST /issuers/{issuerId}/cards/{cardReference}/block-and-replace
Request body :
Changed property replaceCardRequest (object ReplaceCardRequest)
Changed property cardContract (object ReplaceCardRequest.CardContract)
Changed property card (object ReplaceCardRequest.CardContract.Card)
Added property panSequenceNumber (string)
POST /issuers/{issuerId}/cards/{cardReference}/replace
Request body :
Changed property cardContract (object ReplaceCardRequest.CardContract)
Changed property card (object ReplaceCardRequest.CardContract.Card)
Added property panSequenceNumber (string)
POST /issuers/{issuerId}/contracts/create-consumer-contract
Request body :
Changed property contract (object CreateConsumerContractRequest.Contract)
Changed property accountHierarchy (object CreateConsumerContractRequest.AccountHierarchy)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property addCardsAccounts (object CreateConsumerContractRequest.AddCardsAccounts)
Changed property accounts (array)
Changed items (object CreateConsumerContractRequest.Account)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property cardContracts (array)
Changed items (object CreateConsumerContractRequest.CardContract)
Changed property card (object CreateConsumerContractRequest.Card)
Added property panSequenceNumber (string)
GET /issuers/{issuerId}/contracts/external-contracts/{issuerContractExternalReference}/accounts
Response:
Changed property data (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
POST /issuers/{issuerId}/contracts/external-contracts/{issuerContractExternalReference}/add-cards-accounts
Request body :
Changed property accountHierarchy (object AddCardsAccountsRequest.AccountHierarchy)
Changed property accounts (array)
Changed items (object CreateConsumerContractRequest.Account)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property cardContracts (array)
Changed items (object CreateConsumerContractRequest.CardContract)
Changed property card (object CreateConsumerContractRequest.Card)
Added property panSequenceNumber (string)
GET /issuers/{issuerId}/contracts/{contractReference}/accounts
Response:
Changed property data (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
POST /issuers/{issuerId}/contracts/{contractReference}/add-cards-accounts
Request body :
Changed property accountHierarchy (object AddCardsAccountsRequest.AccountHierarchy)
Changed property accounts (array)
Changed items (object CreateConsumerContractRequest.Account)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property cardContracts (array)
Changed items (object CreateConsumerContractRequest.CardContract)
Changed property card (object CreateConsumerContractRequest.Card)
Added property panSequenceNumber (string)
GET /issuers/{issuerId}/customers/external-customers/{issuerCustomerExternalReference}/accounts
Response:
Changed property data (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/customers/{customerReference}/accounts
Response:
Changed property data (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/contract
Response:
Changed property data (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/{accountReference}/contract
Response:
Changed property data (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/card-contracts/external-card-contracts/{issuerCardContractExternalReference}/contract
Response:
Changed property data (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/card-contracts/{cardContractReference}/contract
Response:
Changed property data (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/corporate-contracts/{contractReference}/corporate-employee-accounts/{accountReference}
Response:
Changed property data (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/corporate-contracts/{contractReference}/corporate-employee-accounts/external-accounts/{issuerAccountExternalReference}
Response:
Changed property data (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/corporate-employee-accounts/external-accounts/{issuerAccountExternalReference}
Response:
Changed property data (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/corporate-employee-accounts/{accountReference}
Response:
Changed property data (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
POST /issuers/{issuerId}/corporate-contracts/{contractReference}/add-corporate-employee-cards-accounts
Request body :
Changed property customers (array)
Changed items (object CreateCorporateContractRequest.Customer)
Changed property addresses (array)
Changed items (object CreateCorporateContractRequest.Address)
Changed property addressUsages (array)
Changed items (object CreateCorporateContractRequest.AddressUsage)
Added property entityRequestCorrelationId (string)
Added property entityType (string)
Changed property addCorporateEmployeeCardsAndAccounts (object CreateCorporateContractRequest.AddCorporateEmployeeCardsAndAccounts)
Changed property corporateEmployeeCards (array)
Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
Changed property cardContract (object CreateCorporateContractRequest.CardContract)
Added property requestCorrelationId (string)
Changed property card (object CreateCorporateContractRequest.Card)
Added property panSequenceNumber (string)
POST /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}/add-corporate-employee-cards-accounts
Request body :
Changed property customers (array)
Changed items (object CreateCorporateContractRequest.Customer)
Changed property addresses (array)
Changed items (object CreateCorporateContractRequest.Address)
Changed property addressUsages (array)
Changed items (object CreateCorporateContractRequest.AddressUsage)
Added property entityRequestCorrelationId (string)
Added property entityType (string)
Changed property addCorporateEmployeeCardsAndAccounts (object CreateCorporateContractRequest.AddCorporateEmployeeCardsAndAccounts)
Changed property corporateEmployeeCards (array)
Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
Changed property cardContract (object CreateCorporateContractRequest.CardContract)
Added property requestCorrelationId (string)
Changed property card (object CreateCorporateContractRequest.Card)
Added property panSequenceNumber (string)
GET /issuers/{issuerId}/contracts/external-contracts/{issuerContractExternalReference}
Response:
Changed property data (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/contracts/{contractReference}
Response:
Changed property data (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/accounts/external-accounts/{issuerAccountExternalReference}/corporate-contract
Response:
Changed property data (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
GET /issuers/{issuerId}/accounts/{accountReference}/corporate-contract
Response:
Changed property data (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
GET /issuers/{issuerId}/card-contracts/external-card-contracts/{issuerCardContractExternalReference}/corporate-contract
Response:
Changed property data (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
GET /issuers/{issuerId}/card-contracts/{cardContractReference}/corporate-contract
Response:
Changed property data (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
GET /issuers/{issuerId}/corporate-contracts/{contractReference}
Response:
Changed property data (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
GET /issuers/{issuerId}/corporate-contracts/external-contracts/{issuerContractExternalReference}
Response:
Changed property data (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
POST /issuers/{issuerId}/corporate-contracts/create-corporate-contract
Request body :
Changed property customers (array)
Changed items (object CreateCorporateContractRequest.Customer)
Changed property addresses (array)
Changed items (object CreateCorporateContractRequest.Address)
Changed property addressUsages (array)
Changed items (object CreateCorporateContractRequest.AddressUsage)
Added property entityRequestCorrelationId (string)
Added property entityType (string)
Changed property corporateContract (object CreateCorporateContractRequest.Contract)
Changed property accountHierarchy (object CreateCorporateContractRequest.AccountHierarchy)
Changed property hierarchyOutgoingCreditTransferFeature (object CreateCorporateContractRequest.HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property addCorporateEmployeeCardsAndAccounts (array)
Changed items (object CreateCorporateContractRequest.AddCorporateEmployeeCardsAndAccounts)
Changed property corporateEmployeeCards (array)
Changed items (object CreateCorporateContractRequest.CorporateEmployeeCard)
Changed property cardContract (object CreateCorporateContractRequest.CardContract)
Added property requestCorrelationId (string)
Changed property card (object CreateCorporateContractRequest.Card)
Added property panSequenceNumber (string)
POST /search-contracts
Response:
Changed property data (array)
Changed items (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
POST /issuers/{issuerId}/contracts/search
Response:
Changed property data (array)
Changed items (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/customers/external-customers/{issuerCustomerExternalReference}/contracts
Response:
Changed property data (array)
Changed items (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/customers/{customerReference}/contracts
Response:
Changed property data (array)
Changed items (object Contract)
Changed property accounts (array)
Changed items (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
GET /issuers/{issuerId}/companies/{customerReference}/corporate-contracts
Response:
Changed property data (array)
Changed items (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
GET /issuers/{issuerId}/companies/external-customers/{issuerCustomerExternalReference}/corporate-contracts
Response:
Changed property data (array)
Changed items (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
POST /search-corporate-contracts
Response:
Changed property data (array)
Changed items (object CorporateContract)
Changed property corporateContractEntities (array)
Changed items (object CorporateContractEntity)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property rootAccount (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property insuranceContracts (array)
Changed items (object InsuranceContract)
Added property insurancePackage (object)
Changed property corporateEmployeeAccounts (array)
Changed items (object CorporateEmployeeAccount)
Changed property account (object Account)
Changed property hierarchyOutgoingCreditTransferFeature (object HierarchyOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
Changed property accountOutgoingCreditTransferFeature (object AccountOutgoingCreditTransferFeature)
Added property octOnContractTerminationType (string)
What's Deprecated
No API deprecated.
WERO Refund Processing
As part of the transaction processing we offer secure Refund Processing for Wero payments. The refund option for Wero payments is currently in development, the design of the API can change during this period.
Refunds are reversal transactions wherein complete or partial money is moved back to customer’s source account (account from which actual payment was made). Refund can only be created for a successful or settled transaction:
Customer initiated refunds (returns or cancellation) - E.g. if the Customer has changed his mind about consumption of product pre/post order delivery.
Acceptor initiated refunds - e.g. if a product/service is out of stock or there is a
mismatch in transaction status between payment and Acceptor wherein transaction is failed state at merchant's end but is successful at payments end.
Post Refund (Beta)
Endpoint: POST /refund
The base URL for the payment initiation service API is: /xs2a/routingservice/services/ob/pis/v3
Data model
Legend
| |
| Request (click to enlarge) | Response (click to enlarge) |
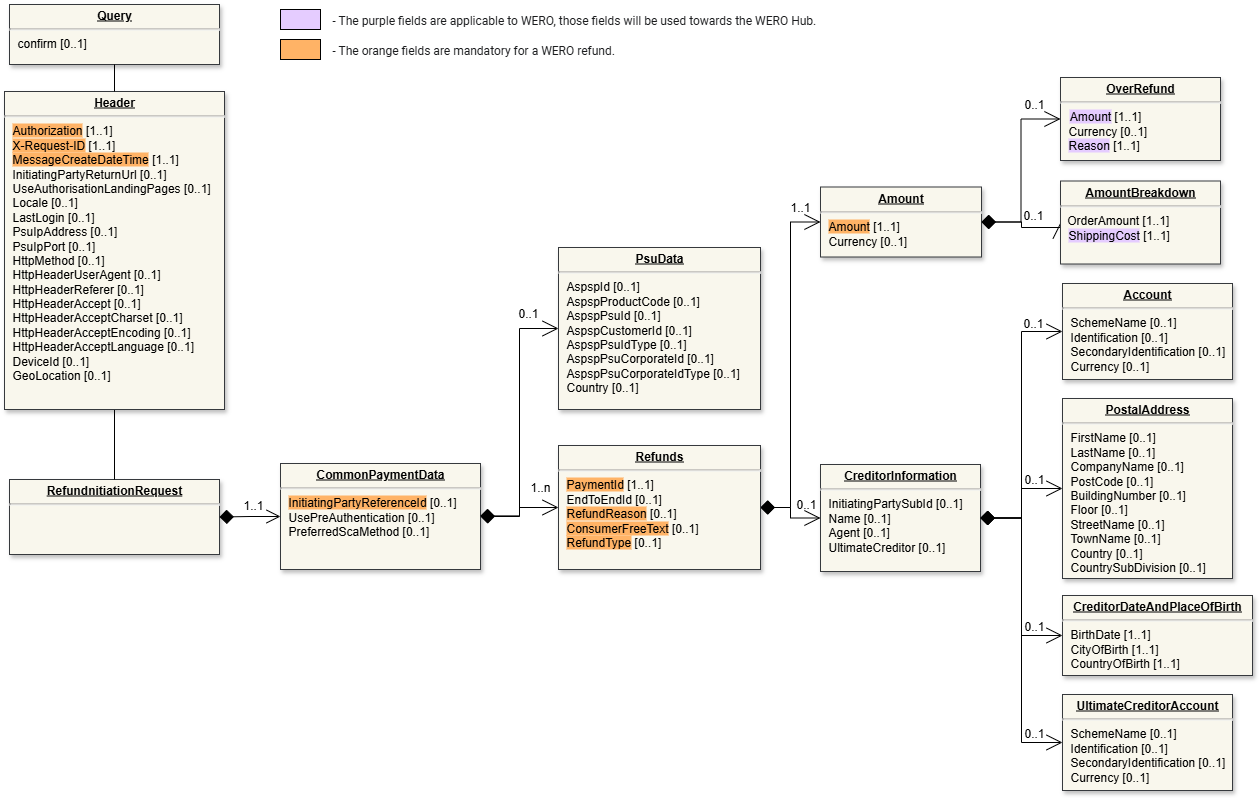 |  |
WERO Notification API
The WERO payment APIs described in this chapter need to be implemented on the Acceptor side, if the Acceptor decides to use them. The Open Banking Service will post notifications to these endpoints. For the WERO product, the post status notification is part of the product.
POST Status
Endpoint: POST /status
This API will notify the Acceptor about the status of the payment.
- The purple fields are applicable to WERO.
- The orange fields are mandatory for a WERO payment.
More details about the fields can be found in the API reference.
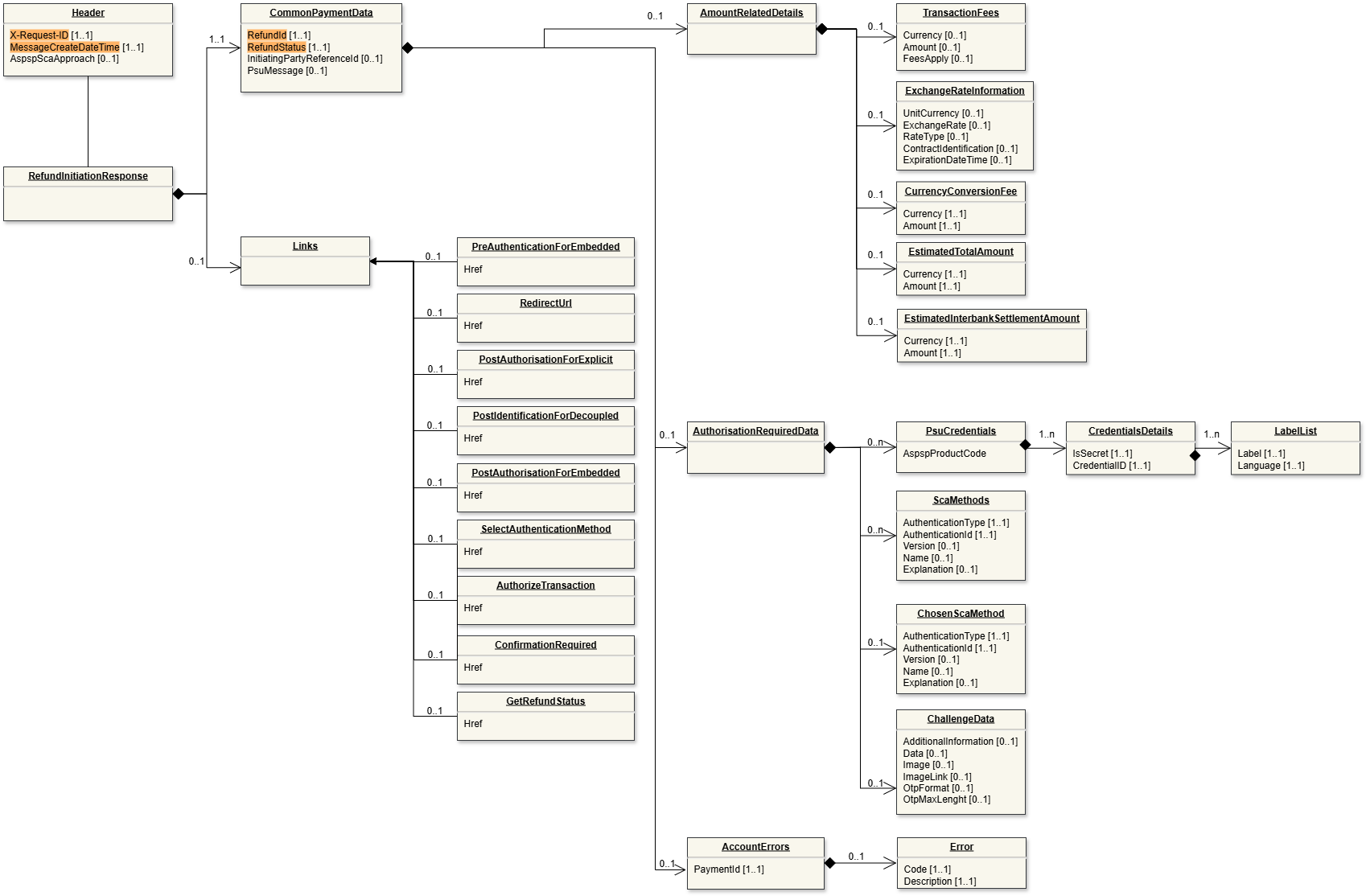
Data model
Below is a representation of the API request and response structure.
Request (click to enlarge) | Response (click to enlarge) |
 |  |
WERO Payment Initiation API
The WERO payment api uses a subset of the available open banking API's. In this chapter only the api's needed for WERO payment initiation are described, furthermore the fields applicable to a WERO payment are marked purple (optional) and orange (mandatory) in the data models.
Payment Status
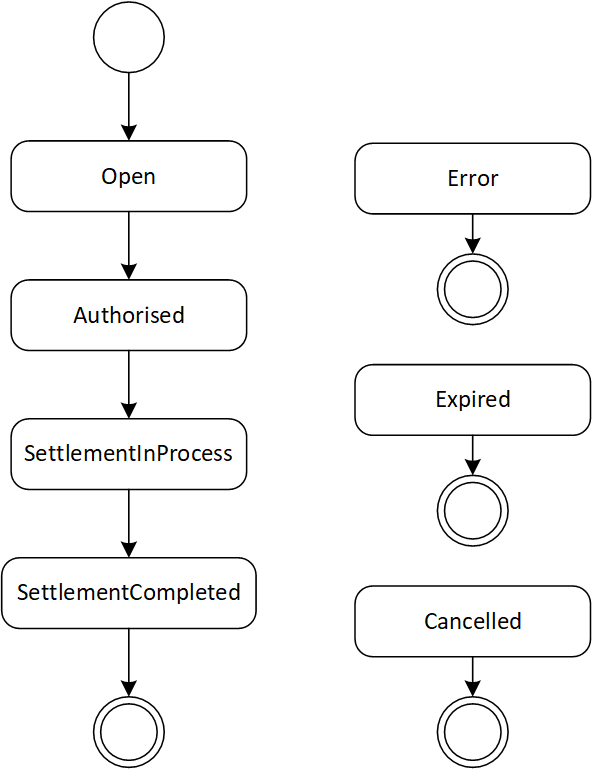
The following statuses are used to describe the actual state of processing:
- Open
- Authorised
- SettlementInProcess
- SettlementCompleted
- Cancelled
- Expired
- Error
In the following picture the possible WERO status are shown in an activity diagram:
Status mapping to Wero
The following table describes the mapping from the Wero payment status(es) to the unified payment status used in the Open Banking Platform. A Wero Single immediate payment consists of a consent, authorization and capture resource, each have an individual status. The combination of those statuses is mapped to a single Payment status in the Open banking solution.
| Worldline | Wero Consent | Wero Authorization | Wero Individual Capture |
|---|---|---|---|
| Open | Requested or Granted | ||
| Authorised | Granted | Granted | |
| SettlementInProcess | Granted | Granted | Accepted |
| SettlementCompleted | Granted | Granted | Settled |
| Cancelled | Denied | ||
| Cancelled | Granted | Rejected | |
| Cancelled | Granted | Cancelled | |
| Expired | TimeOut | ||
| Error | Granted | Failed |
POST Payments
Endpoint: POST /payments
Base URL: /xs2a/routingservice/services/ob/pis/v3
This endpoint is used by the Acceptor to initiate a WERO transaction.
- The purple fields are applicable to WERO.
- The orange fields are mandatory for a WERO payment.
More details about the fields can be found in the yaml specification.
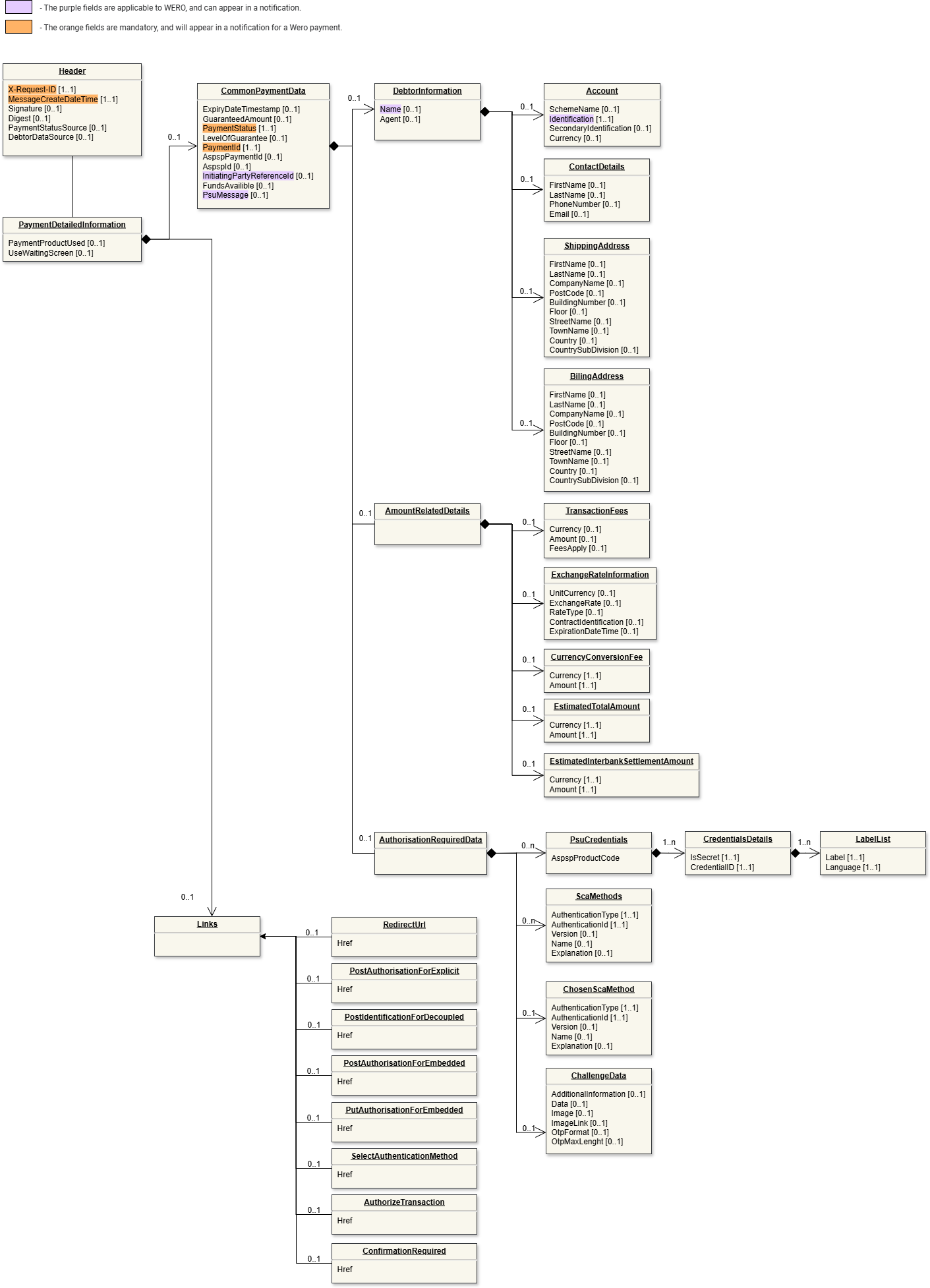
Data model
Below is a representation of the API request and response structure.
Request
Legend
| |
| Request (click to enlarge) | Response (click to enlarge) |
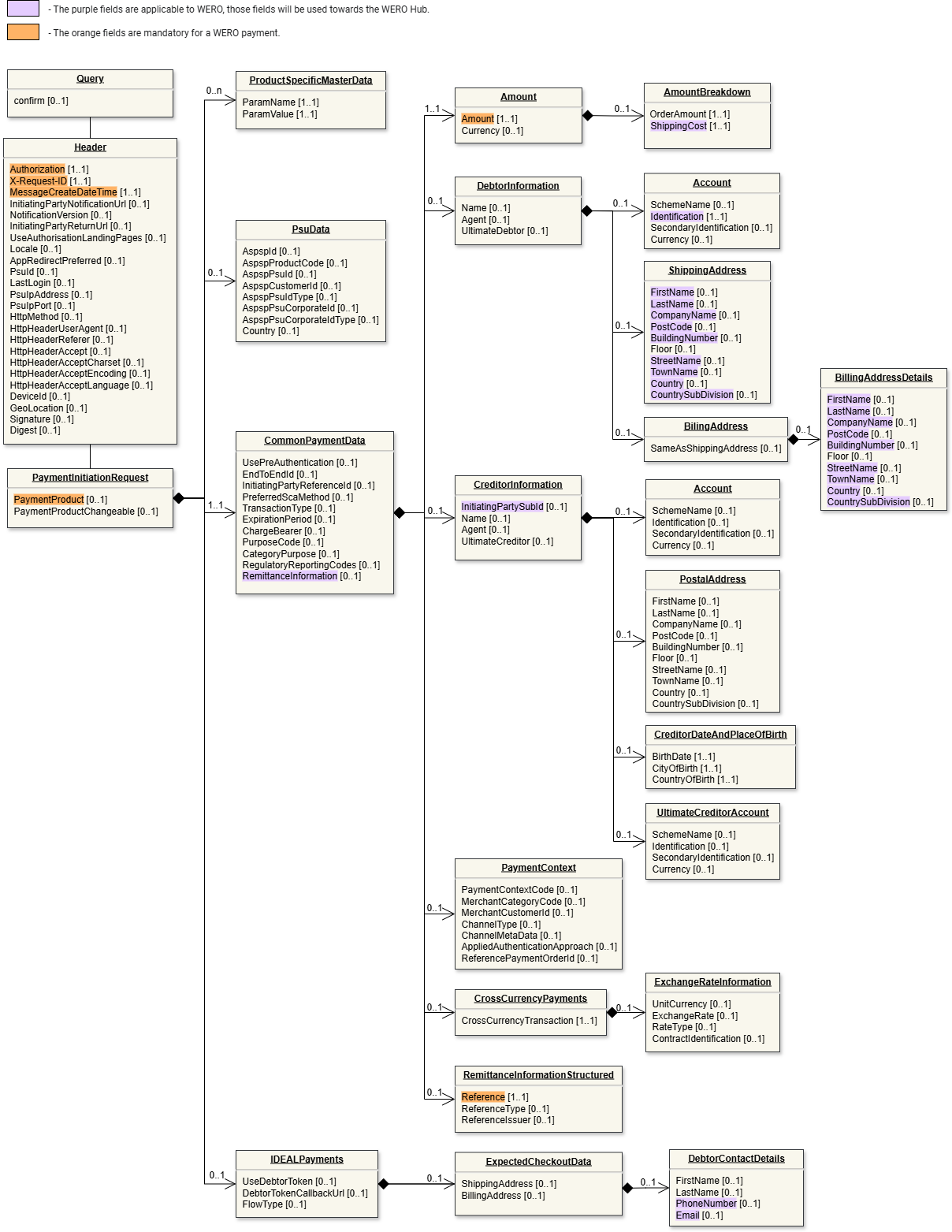 | 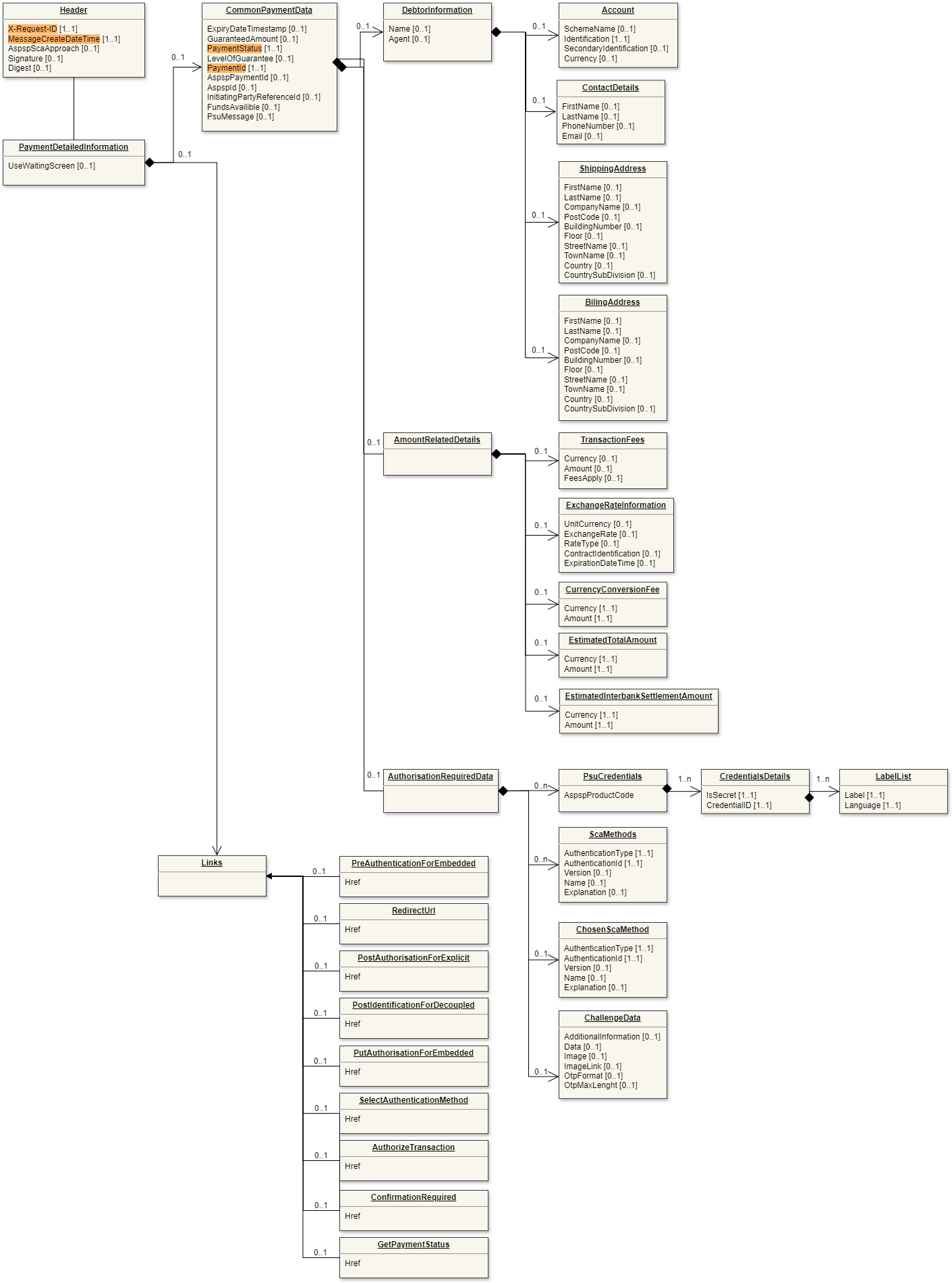 |
Example: WERO Single Immediate payment
Request:
Address: https://localhost:8443/xs2a/routingservice/services/ob/pis/v3/payments
HttpMethod: POST
Headers: {X-Request-ID=27965d49-b27b-38a9-6f7a-2211cb5c0c78, Authorization=Bearer 69eb307c55eb91b4a4144ec8a2d8562d, MessageCreateDateTime=2022-03-22T14:02:13.184Z, Digest=SHA-256=DZ0QKHaRy/MdbWEI62wuE7xJMrfJJBTUWF8irHIHTGw=, Signature=keyId="8D0F688AD3E6C2D4D5FB99FE129F2A2E3B496AF7",algorithm="SHA256withRSA",headers="x-request-id (request-target) digest messagecreatedatetime",signature="DK7sQCW56EMXHOw/rdW3RlrtM2U/QL2Hy5g5Fsq+oZ0qspiDerzYL0FRu47EdGWT9qy7n7R3ay6iJHVCUrgFvVXS806E3Clgh5u7+J8/xgUeEPRglA6jeNaLYErKC+xIklJrmpKODDkD407IgA6Y9LhixFisSfawR1pDs2vwOsB1wnujrwBcKFzYf66/pxhW06NZu98VM0pkLm5OFp82G0x4vHfOPAoo46xcSXd/IbQV0DYZewosQIaI5qAclPvmusO9uXDx90uqgDL4E8fLW4yHEaraW7yDlCx54bcraU4ubo+wqDE8NJMKxEVreI/Se9YY73mvAMnOkon1jZHsAQ=="}, Accept=*/*, Content-Type=application/json
Payload:
{
"PaymentProduct": ["WERO"],
"CommonPaymentData": {
"RemittanceInformationStructured": {
"Reference": "12345"
},
"RemittanceInformation": "Example payment",
"Amount": {
"Amount": "100.00",
"Currency": "EUR"
}
}
}Response:
ResponseCode: 201
Headers: {X-Request-ID=0e1b8b7d-2438-4bb0-acf5-d68f967c8b25, MessageCreateDateTime=2022-03-22T14:02:13.694Z, Digest=SHA-256=gJNKvdO+dlRlWyevVFfDeEAAJDtmw41A3pQOyNX3K6o=, Signature=keyId="3EBEF6033C00730D9C6DA05165A3CAA1F31036FB",algorithm="rsa-sha256",headers="messagecreatedatetime x-request-id digest",signature="NMQImrvrg664n3rBCF9s8fQLvZVH/zPsHfzzxJ671BWz6fvjtn81Arv6TPd8N6/nLLNNjY23YubI33tYDjyEf1vq1wF3vq/gFqmF2s66dxHFy7Gd9mOEdpxc0BYCwpG2ozntRvnrIv2z9SXFlKljc6OT+mqLo+vCB8Gn6frdrwGgZqY6uHOEh3rPvYJ/nWTHQkfxzx/U624wqtuoI8Va4kIXM2pPBCPo4AAq2hFXtj4Okh5vFmRlRiIM9CFgfO+5k1lMC3YzrmE8aB9CyFoJoT3e5pSKNePL+hunGlJG6XPg92Hg/gpS06PyvCtHA5585ONkQv+oNhFdpfdtob1qBQ=="}
Payload: {
"CommonPaymentData": {
"PaymentStatus": "Open",
"PaymentId": "1282",
"AspspPaymentId": "0001092688873027"
},
"Links": {
"RedirectUrl": {
"Href": "https://pay.int.epi.engineering/516ca41d-d47a-468a-9726-8299d69168a9"
}
},
"UseWaitingScreen": false
}GET Payment Status
Endpoint: GET /payments/{paymentId}/status
This endpoint is used to retrieve the status of a payment.
Data model
Legend
| |
| Request | Response (click to enlarge) |
 | 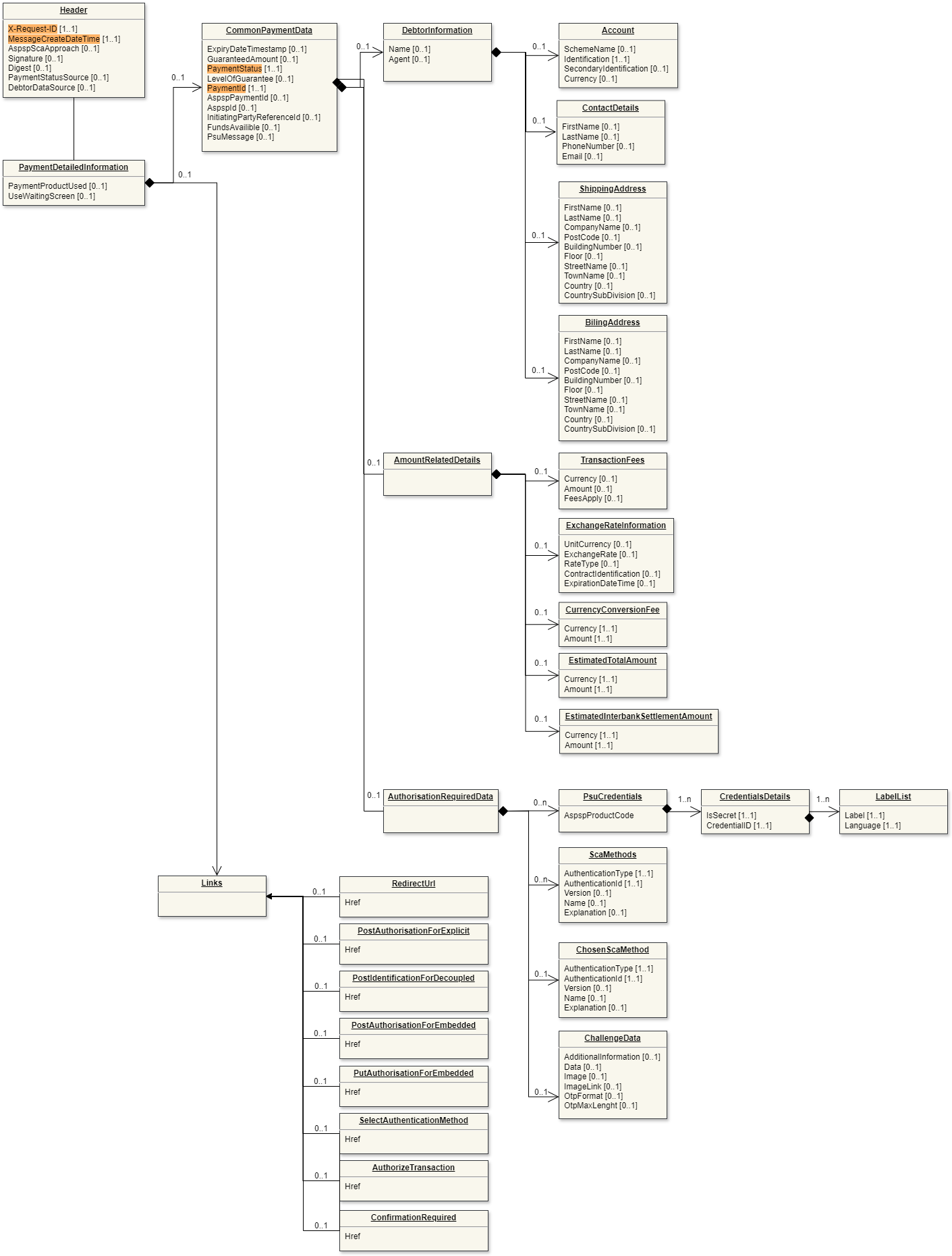 |
Example: WERO payment status
Request:
Address: https://digitalroutingservice.awltest.de/xs2a/routingservice/services/ob/pis/v3/payments/1282/status
HttpMethod: GET
Headers: {Accept=application/json, Digest=SHA-256=47DEQpj8HBSa+/TImW+5JCeuQeRkm5NMpJWZG3hSuFU=, X-Request-ID=aa9ec3e7-dc34-f625-2e97-e16644ea1e77, Authorization=Bearer 59519322f1f56db6bd1d23ac0e22cf5015088f085970fb9b461ff2684bc2e96a, MessageCreateDateTime=2024-01-08T12:55:34.630Z, Signature=keyId="39d8e82bb33e7e2a09cbcb3ef3eab351ee1c5e8f",algorithm="SHA256withRSA",headers="x-request-id (request-target) digest messagecreatedatetime",signature="W/6ViHZJ/x0/KM61H7mwCZQp2/3WPax5seqLpCby0BXwgpVoFrSmCu5oHF2pLS2AdHuTiE6qFsBnMkfeGMEDwtqCdY0GZVQGwZ6j9+6zjJHwm21xZ+BmXXH4puRgqxt7DSnOou3SkstzCblf4gSL8MqIyYu7n+eLQlWvjl57t7dNgX0sNTwJE/1GgU/ukDyUoJl4aO1n9ID8EnLDUpXunbZ+1pyCPGbfz5/pDMrJsKZ9l58tLxj7IneU+Mnai8UJEqrQ441ONgYCHF7KoDxu15XA+IY7DnwkA5u/+QN7IY5KpHG3zP19m7jiOimkI6lrqLAc2Ld4iehjNMGve7Ci7w=="}
Response:
ResponseCode: 200
Headers: {X-Request-ID=3a3df5d3-fa9e-4fee-b9fd-067c23dc91fa, MessageCreateDateTime=2024-01-08T12:55:35.032Z, Digest=SHA-256=pV9HQh/XGpLmawhfj9d/hxYucKkOQCKV9BJ978PeW5k=, Signature=keyId="3EBEF6033C00730D9C6DA05165A3CAA1F31036FB",algorithm="rsa-sha256",headers="messagecreatedatetime x-request-id digest",signature="DMvxRTvhRG1kFAy0JPbBzdoRrXq5C9OUJHl6GMQkdNriG4SeuHGaFpdaDA6NgFw2+Ky/RBYiruL18ul+1ZvmdhlyhMaRqR0J7Jg/m9JMyu3wFunBVINysQ+2yj0ucXRMck/CoBW1mYwjDCGCN7xOofw2mZLV6PHjP9xHaDA855iPYE7HUaukB/qveA/S6B2qsjFxDs5AJh6VSWEoknA1+NJZCEX2VC23bnkMgy92qN6bZch5bL3462yFA/0uA75k9XH3O7+Jesl86tBU3kKATNk5n2//vun+Bg4NlSQjU21m6B+nOZT1M+TUkVzG0KWdByf6yFv/x0rp7hifnFZvjA==", Date=Mon, 08 Jan 2024 12:55:35 GMT, Content-Type=application/json;charset=UTF-8}
Payload: {
"PaymentProductUsed": "WERO",
"CommonPaymentData": {
"PaymentStatus": "SettlementCompleted",
"PaymentId": "1282",
"AspspPaymentId": "0001092688873027",
"AspspId": "10002",
"InitiatingPartyReferenceId": "7cc080484bd74d2c8c1d8d2b296ee5b9"
}
}
WERO Transaction Flow
This page describes the transaction flows for WERO payments, designed to provide a seamless payment experience whether accessed via the WERO mobile app or through bank-integrated solutions.
Which Wero Payments are supported?
- Single Immediate Payments
More Wero payment plans will be added in the future.
In the paragraphs below you can find a brief explanation of the payment flows from the Consumer perspective and from the Acceptor's (technical) perspective.
WERO flow from the Consumer perspective
What is the difference between an e-commerce and m-commerce flow?
The flows differ in how the redirection between the online shop and the Wero digital wallet happens:
- in the e-commerce flow (web storefront checkout (desktop or mobile web), a Wero landing page is displayed with a QR code for linking the online shop to the Wero digital wallet.
- in the m-commerce flow (shop and pay in smartphone), the wallet is launched automatically after tapping the "pay with Wero" button, and no QR code is needed.
The actual WERO transaction flow that the Consumer follows depends on where the payment authorization takes place (in a standalone Wero wallet or in the Consumer PSP's app) And if a Consumer is already registered for WERO.
Below you'll find an example screen flow of the e-commerce flow for a Wero single immediate payment:
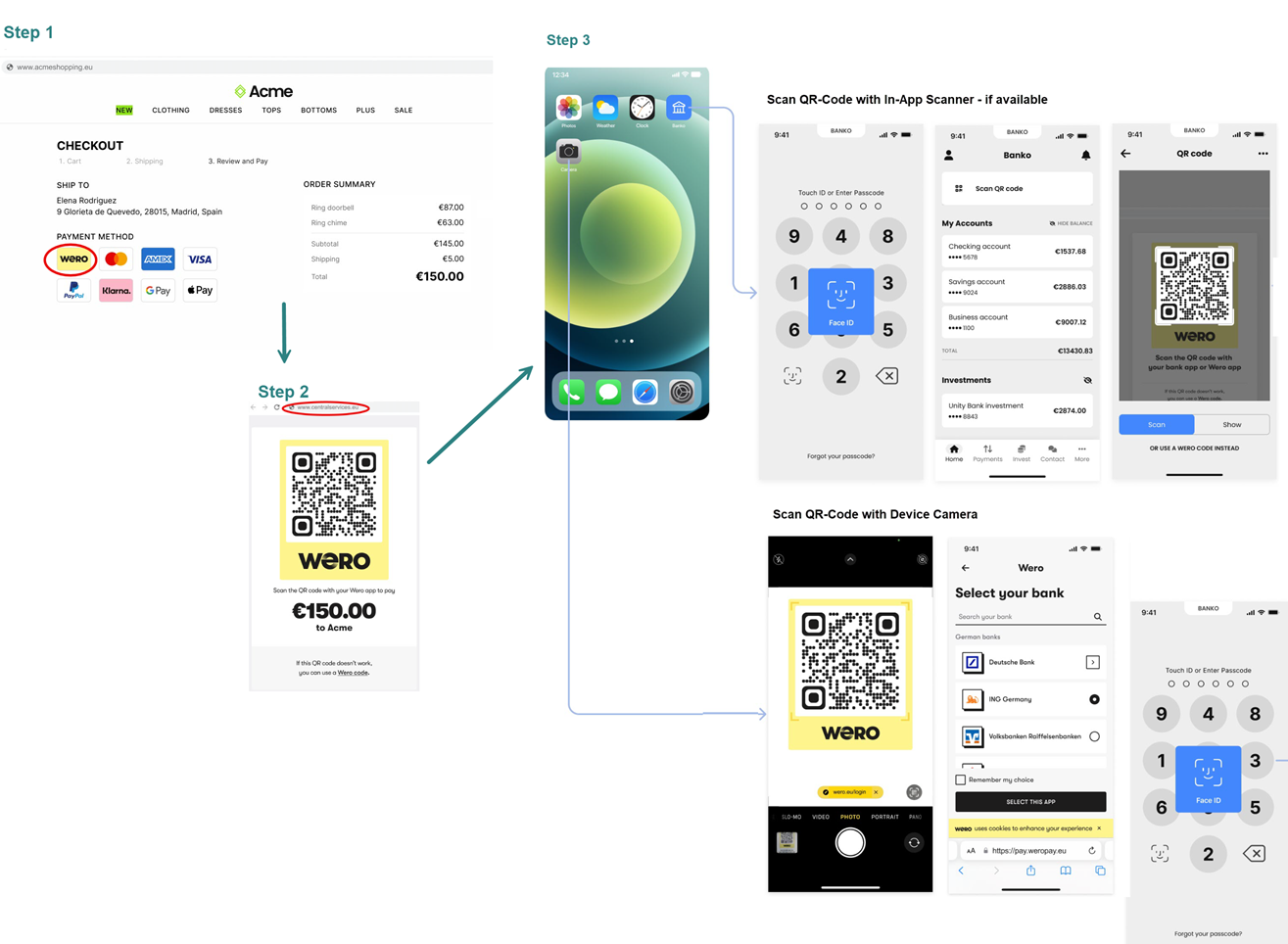
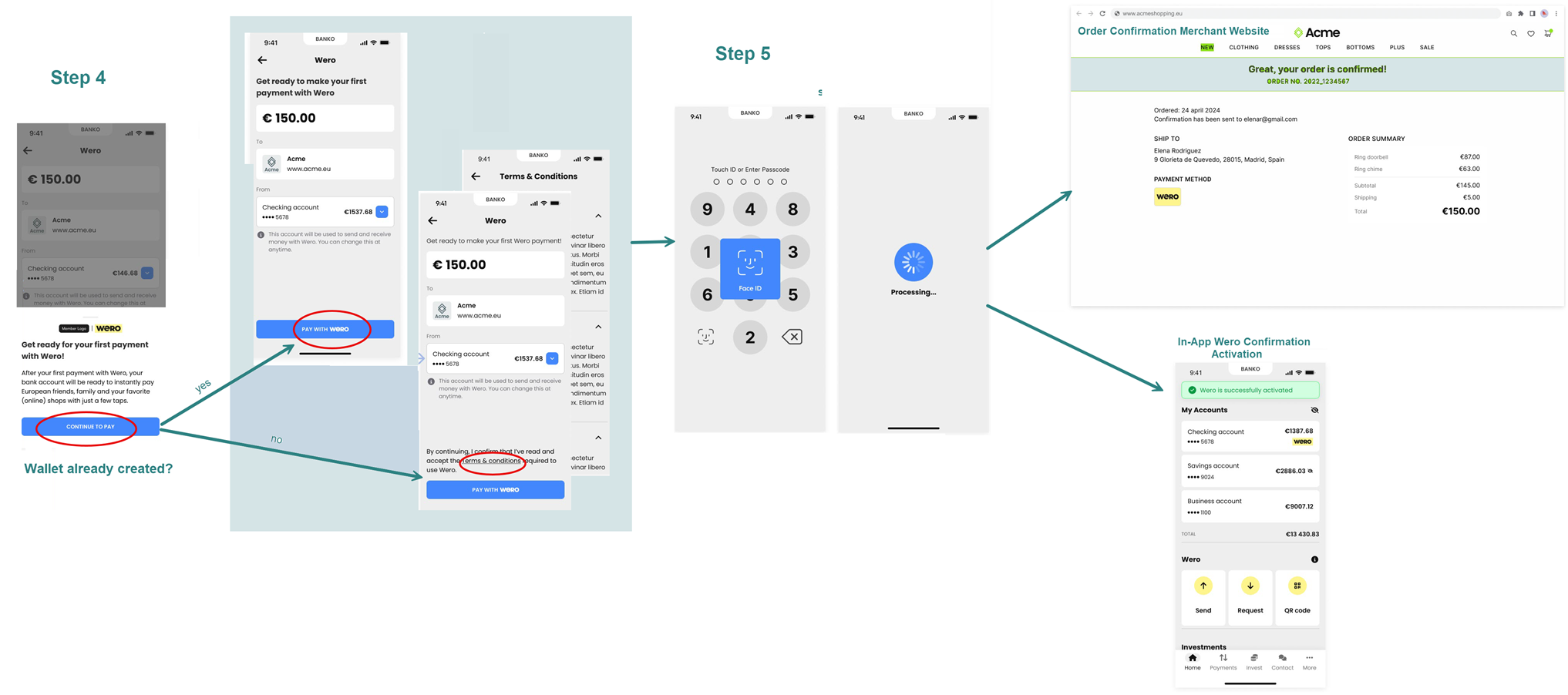
The Consumer flow does not impact the integration between the Acceptor and the Worldline Open Banking Solution.
Wero flow from the Acceptor perspective (technical)
WERO Single Immediate Payment
In the diagrams below, the sequence of requests is shown to initiate a Wero Single immediate payment. The vertical green bars indicate which party is responsible for the session of the Consumer. If a party has the session, a screen can be displayed. Notice that in the WERO flow, the Acceptor can receive a notification when the authorization of the payment is finished on the Consumer PSP side. To receive this notification, the Acceptor should implement the Post status API, so that this can be called by the Open Banking Service. The Acceptor also has the option to request the status by calling the Get /payments/status API of the Open Banking Service.
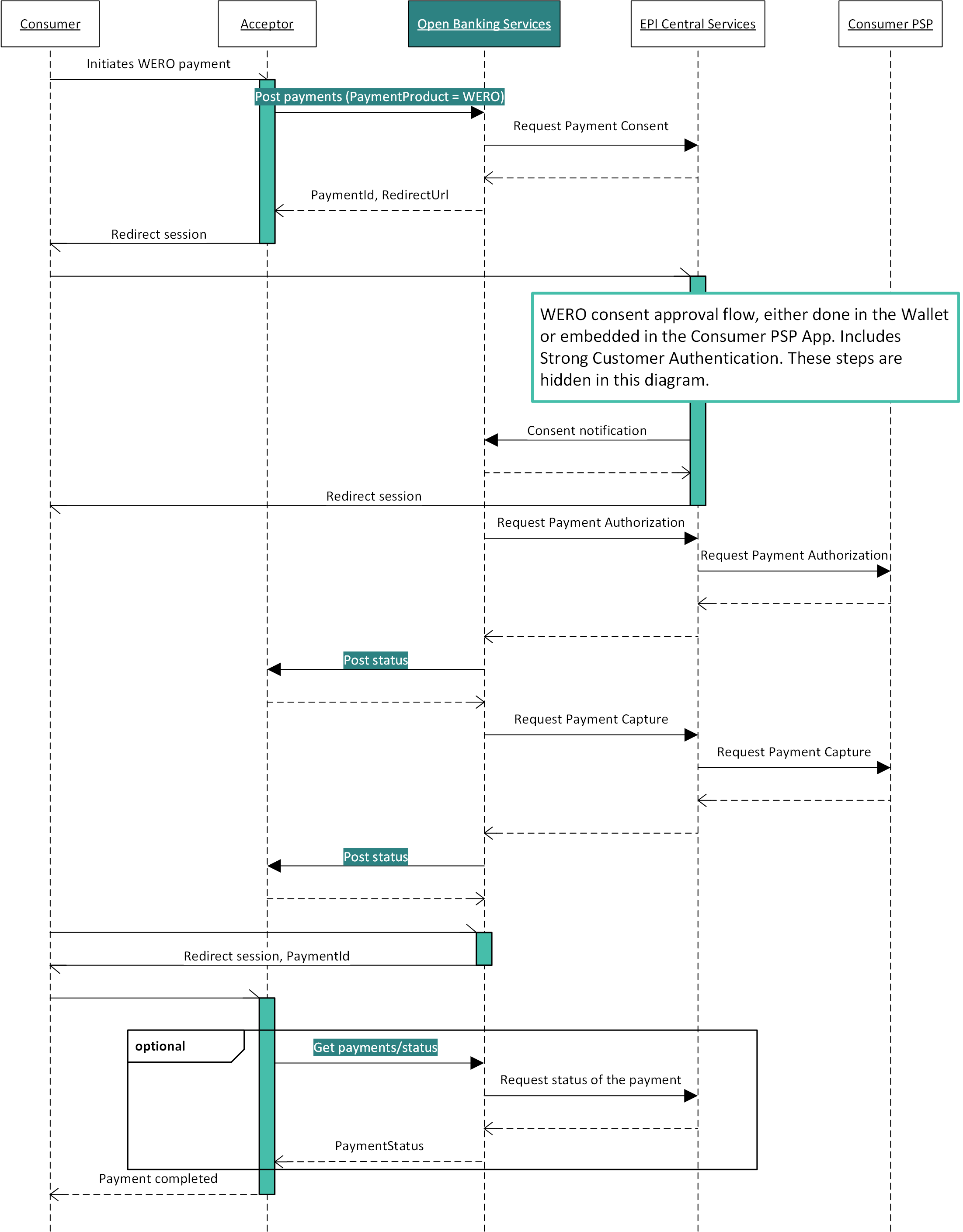
WERO
These pages describe the components from the Open Banking API version 3 which are used to initiate a WERO payment. WERO is an European payment system created by the European Payments Initiative (EPI). It helps facilitate quick, secure, and straightforward bank-to-bank (A2A) transactions for individuals and companies.
If you would like to learn about the various ways WERO can be used, we recommend visiting this very informative interactive website: Wero - Digital Payment Wallet. The page is published by EPI - owner of the Wero brand - and presents practical use cases for individuals and businesses, offers interactive demos to explore how it works, and provides step-by-step guidance to get started, including onboarding paths and deployment timelines, plus essential privacy and security notes.
Here you learn, how Worldline simplifies the WERO flow - one single API, which is used for nearly all payment means, does all needed steps (consent, authorization, capture) in one single call for you.
Ecosystem overview
The Open Banking Services, marked in green, is provided by Worldline. The Consumer interacts with the Acceptor to start a payment. He is redirected to their Wallet to authenticate/authorize. The Wallet communicates with the EPI Central Services via the Wero API. The Acceptor uses the OB v3 API to talk to Open Banking Services / Acceptor PSP. The EPI Central Services coordinates between the Wallet and the Open Banking Services / Acceptor PSP using the Wero API.
With the Open Banking Service Worldline is a Technical Solution Provider (TSP) within the Wero scheme, providing it's services to the Acceptor PSP. Thereby enabling the Acceptor PSP and it's Acceptors (Merchants) to provide the Wero payment product.
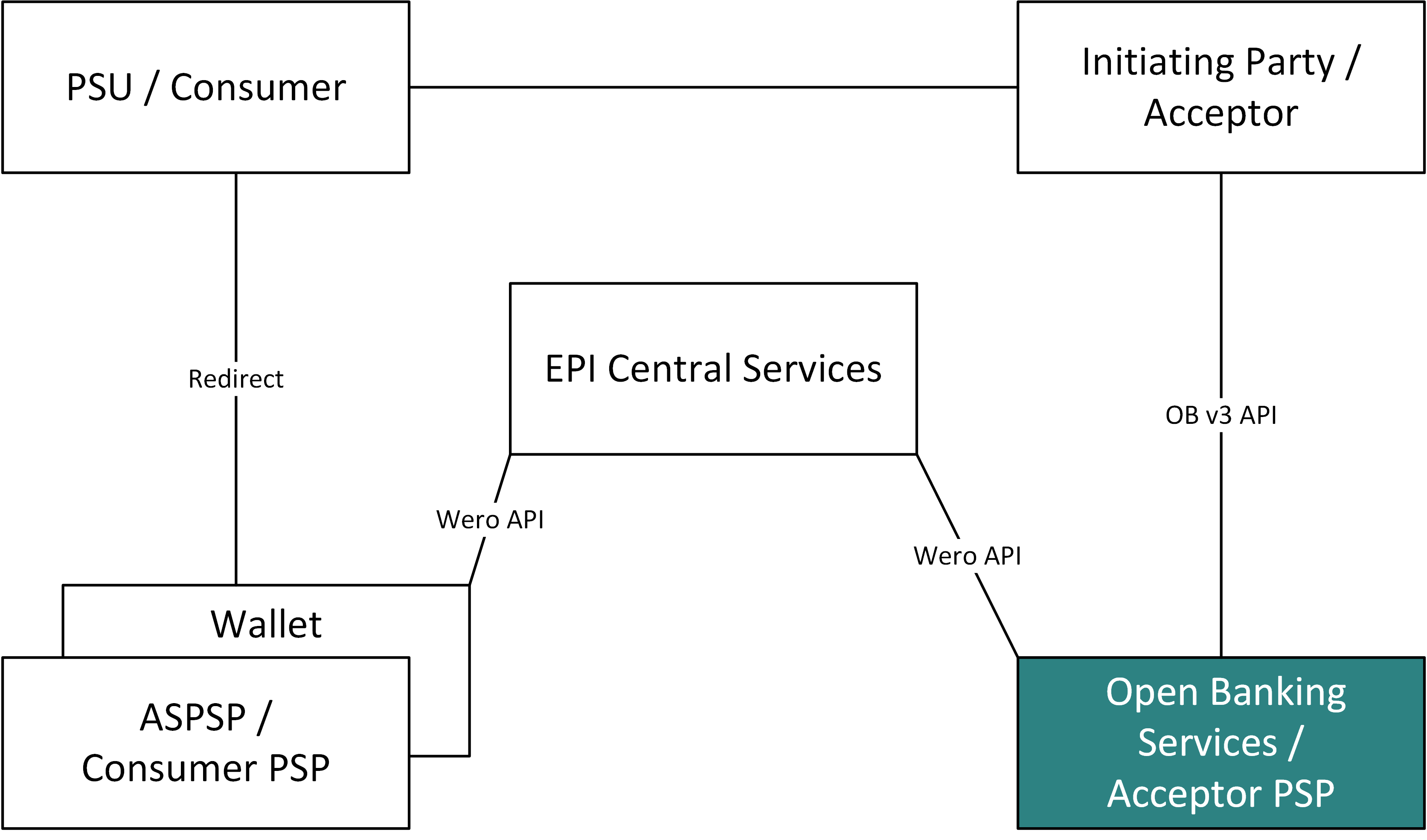
Terminology
The terminology used in these pages and the mapping to their Payment Service Directive 2 equivalents.
| Term | Equivalent PSD2 term | Description |
|---|---|---|
| Consumer PSP | ASPSP | The Account Servicing Payment Service Provider (ASPSP); the Issuer bank which is responsible for the Consumer's account. |
| EPI | European payments initiative (EPI Company | Home), owner of both the iDEAL and Wero brand. EPI provides an EPI Central Services hub which connects to the participants of Wero. | |
| Acceptor | Initiating Party | The Acceptor contracts the TSP for the WERO service, and sends a WERO payment request to the Open Banking Service on behalf of a Consumer. |
| Consumer | PSU | The Consumer is account holder by one or more Consumer PSP's and allows other parties to initiate payment requests. |
| SCT Inst | The SEPA Instant Credit Transfer is the underlying instant-settlement infrastructure that powers WERO’s real-time payments across Europe. Payments are settled in seconds, available 24/7/365, for transfers between participating banks across the SEPA region. | |
| Technical Service Provider (TSP) | TPP | The Technical Service Provider (TSP) can be contracted by acceptor PSPs or consumer PSPs and be authorised to participate in the payments flow. The 'Open Banking Service' refers to the Worldline provided software, which handles the routing of the WERO payments for the Acceptor PSP. |
| Wallet | The Wero wallet can be a standalone app or can be access through the Consumer PSP's bank app. | |
| WERO | We - Euro, is the new pan European payment system created by the European Payments Initiative (EPI), which will replace iDEAL and other national payment products. It is designed to enable fast, secure payments for individuals and businesses, can be accessed via bank apps or a dedicated mobile app, and aims to become Europe’s standard for digital payments. | |
| EPI Central Services | The EPI Central Services operates as the centralized control point for WERO payments, ensuring end-to-end coordination across participants. |
Open Banking API features for WERO payments
WERO will support different payments plans, at the moment the following is supported:
- Single Immediate Payment: For a successful single, immediate payment, the Consumer is strongly authenticated and consents to one payment. The payment is immediately authorized and captured. The money is settled immediately using the SEPA SCT Inst rail.